Secure Code Review
- Home
- Secure Code Review
What is Secure Code Review?
Secure Code Review In our penetration testing methodology, we follow a meticulously designed process for identifying and prioritizing the most vulnerable parts of your network. Accordingly, we recommend actionable solutions to our clients. The chief objective of running a network penetration test is to identify exploitable vulnerabilities in networks, network devices, systems, and hosts so that such vulnerabilities are fixed before any hacker can detect and misuse them.
Network penetration testing helps in detecting critical vulnerabilities that can potentially enable hackers to compromise systems, gain unauthorized access to sensitive data and even take over systems for malicious purposes.
Talk To A Security Expert
We Will Help You To Choose The Best Plan!
Need for a Secure Code Review
Security source code review helps an enterprise in minimizing the overall maintenance and development cost enhancing the effectiveness of the code lines and eliminating any kind of early-stage risks. In many industries such as healthcare, financial services, e-commerce, etc., secure code reviews are a mandatory part of the compliance requirements. It also offers an added layer of benefit to the security of the application, prior to its release. Code Ekte’s robust secure code review offerings will help you accelerate review timelines and will seamlessly enhance the cost-effectiveness of the security verification process.
Industry’s Best Security Standards
Our team of experts uses practices that involve the industry’s best security standards including:
What is the advantage of Code Review?
- The design and framework implementation is consistent with the required structure of the application.
- Bugs are found at an early stage, which prevents any major setback that is bound to occur in the future.
- The codes get optimized, which in turn, improves the performance and user experience.
- It instills confidence in stakeholders and improves their participation.
- It allows the application of new techniques and collaborative approaches from the development team.
- It allows the fulfilment of requirements and monitoring enhances the quality of the project.
Code ekte’s Approach
Our security experts leverage their expertise to deploy a manual and automated inspection to unravel all the possible coding errors. Then, they present resolving and solution measures to eliminate those errors.
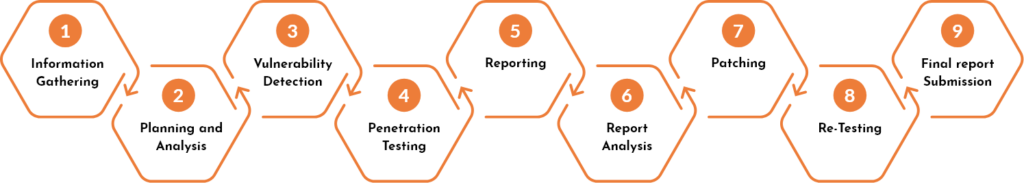
We have a set of dedicated steps involved in the review process. Below are the steps-
Security Testing Methodology

01
RECONNAISSANCE
This is the first step in Secure Code Review where information gathering is done. This requires analyzing secure codes that are built on certain software. Our review team evaluates the codes extensively and provides insights into the application. The insights consist of comprehensive details of libraries and code modules.
02
THREAT ASSESSMENT
The objective of threat assessment is to comprehend the architecture and framework of the software or web-based applications. The identified threats are considered as vulnerabilities, which will be listed in prioritized order of risk. Our review team will identify the vulnerabilities through threat assessment and will recommend the best course of action to resolve them.


03
AUTOMATION
The application of automation is essential for large codebases and multidimensional code structures. Many open source and commercial applications tools are used for automated code review. The basic application of automation is to examine millions of lines of code. The automated tools are quite effective in identifying insecure packets of code. They can be further evaluated by the developer or any security analyst.
04
CODE REVIEW TOOLS
Some of the tools we use for .NET are:
Puma Scan: It is a .NET C# open source static source code analyzer.
.NET Security Guard: It is helpful in security audits on .NET applications. It finds SQL injections, LDAP injections, XXE, cryptography weakness, XSS, and more.
Secure Assist: It prevent insecure coding and configurations (.NET) by scanning code automatically as an IDE plugin for Eclipse, IntelliJ, and Visual Studio, etc.


05
MANUAL CODE REVIEW
Manual code review is quite important to examine key security controls. It allows verification of encryption, logging, data protection, access control, usage, and back-end communication system. The manual review is also important for identifying the flow of data and tracking the application’s attack surface. Going through the code line by line is expensive and time-consuming, but it gives better clarity of the code and also helps in removing the false positives.
06
CONFIRMATION & POC
When all the above steps are completed, we put every finding in a report in an understandable format. We put every issue in the code and the patching solution against it. The issues and recommendations are discussed between the client’s development and Kratikal’s security team and accordingly development team fixes it.


07
REPORTING
After completing all these steps, our team prepares the report which consists of all the findings in a simple and understandable format. The team represents all the fragments and modules of code where risks or issues exist. At the same time, our team also documents the patching solution against each vulnerability. The report also contains the list of recommendations after conducting a discussion between Kratikal’s team and the client’s development team.
Frequently Asked Questions
Browse through the FAQs given below to find answers to the commonly raised questions related to the VAPT services
A secure source code review is a process of identifying and patching coding errors in the development phase before they turn into a high-level security risk. It helps in identifying hidden vulnerabilities, design flaws, insecure coding practices, backdoors, injection flaws, cross-site scripting bugs, weak cryptography, etc.
The importance of secure code review is to identify and locate security-related vulnerabilities and flaws within the source code. These flaws can be malicious and might make the whole code hostile for exploitation. If the source code of applications is not secure, then it might compromise the integrity, security, confidentiality, and attainability of the applications.
The advantages of Code Review are –
- The design and framework implementation is consistent with the required structure of the application.
- Bugs are found at an early stage, which prevents any major setback that is bound to occur in the future.
- The codes get optimized, which in turn, improves the performance and user experience.
- It instills confidence in stakeholders and improves their participation.
- It allows the application of new techniques and collaborative approaches from the development team.
- It allows the fulfilment of requirements and monitoring enhances the quality of the project.
The significance of peer review in software testing is to inculcate a disciplined and technical application of software development. The objective of peer review is to identify the defects and correct them by preventing leaks. A peer review in software testing is also referred to as static white box testing because of its implication in the early stages of software development.
The concept of secure SDLC is to imply best programming and development practices to enhance security in the Software Development Life Cycle. The notion of security is implied at each phase of SDLC which requires engineers from the development team to focus on the element of security. This provides additional focus on the structure of the application before its deployment.









