Network Security Testing
- Home
- Network Security Testing
What is Network Security Testing?
Network security testing In our penetration testing methodology, we follow a meticulously designed process for identifying and prioritizing the most vulnerable parts of your network. Accordingly, we recommend actionable solutions to our clients. The chief objective of running a network penetration test is to identify exploitable vulnerabilities in networks, network devices, systems, and hosts so that such vulnerabilities are fixed before any hacker can detect and misuse them.
Network penetration testing helps in detecting critical vulnerabilities that can potentially enable hackers to compromise systems, gain unauthorized access to sensitive data and even take over systems for malicious purposes.
Talk To A Security Expert
We Will Help You To Choose The Best Plan!
Network Penetration Testing Methodology
Each organization infiltration test directed by Kratikal includes the utilization of around the world acknowledged and industry-standard systems. At least, the hidden structure depends on the Penetration Testing Execution Standard (PTES) and National Institute of Standards and Technology (NIST) and goes far past the underlying system itself.
This includes the examination of weaknesses, which incorporates investigating the result from different security apparatuses and manual testing procedures. An organization weakness appraisal comprises of a wide scope of undertakings, for example,
- Recognizing, focusing on and measuring network dangers
- Security control checks
- Breaking down network strength against different organization based assaults like neighborhood advantage assaults, network interruption, port filtering, animal power assaults, and so on
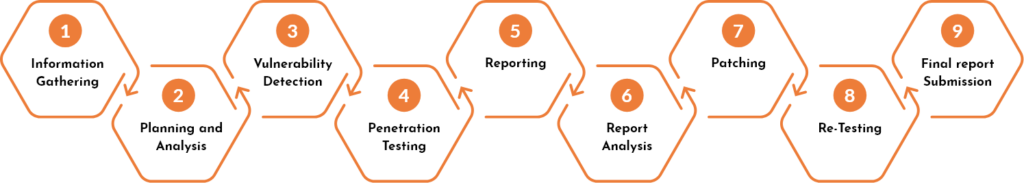
Security Testing Methodology
01
Wireless VAPT Methodology
After the initiation of the venture, target data will be given by the customer. In instances of remote infiltration testing, the gathered data will comprise of a rundown of all SSIDs and MAC Addresses in scope. This data helps the Tester in discovering which passages are represented and which ones are rebel passageways. Furthermore, at this phase of testing, a rundown of the relative multitude of areas and structures is gathered before the task is booked.
- Site Survey
- Unauthorized Access Attempts
- Post-Authentication
Once our assessment is complete, we deliver a detailed network analysis and executive summary that includes effective remediation steps. We strive to provide clear and concise reports that include the following:
- Executive Summary
- Identified Vulnerabilities and Risk Ratings
- Detailed Risk Remediation Steps
Planning / Execution

Windows-Based System Config Audit Test Cases

Linux-based System Config Audit Test Case

SQL Database Config Audit Test Case
02
Configuration Auditing Methodology
The motivation behind this technique is to assess the security of an association’s frameworks involving the security review to distinguish weaknesses in the frameworks. Our evaluating technique goes past the location cycle of basic checking programming. We distinguish and focus on the most weak spaces of your arrange and suggest significant arrangements.
After initiating the project, scoping/target information will be collected from the client. In the case of a Windows/ Linux/another type of server configuration review, this information will include:
- IP Addresses of the Systems/Servers in scope
- Read-Only Administrator-level credentials (we want to see all configuration settings without the ability to modify)
- Any required access information (e.g., we will need VPN credentials to your internal network before we can access it)
Planning / Execution

Security Configuration Review

Linux-based System Config Audit Test Case
Firewall Auditing Test Case

Reporting
03
Firewall Auditing Methodology
After initiating the project, scoping/target information will be collected from the client. In the case of a firewall configuration review, this information will include:
- IP Addresses and/or URLs for the firewalls in scope
- Read-Only Administrator-level credentials
- Any required access information (e.g., we will need VPN credentials to your internal network before we can access it)
Planning / Execution

Security Configuration Review
Router Auditing Test Cases

Reporting
04
Router Auditing Methodology
After initiating the project, scoping/target information will be collected from the client. In the case of a router configuration review, this information will include:
- Configuration files of routers in scope
- Any additional requirements
Planning / Execution

Security Configuration Review

BYOD Auditing Test Case

Reporting
05
BYOD Configuration Methodology
The scope of this section is limited to configuring and reviewing the onboarding process of BYOD. It assumes that the BYOD onboarding process (e.g., ISE) is already up and running, configured with certificates, and integrated with Active Directory
After initiating the project, scoping/target information will be collected from the client. In the case of a BYOD configuration review, this information will include:
- All the device information in scope
- Any additional requirements
Tools Used
We use industry benchmark security testing tools across each of the IT infrastructure as per the business and technical requirements.
Below are few from many of the tools we use:
Burpsuite
Nipper
Nmap
Nikto
Metasploit
OpenVAS
Aircrack-ng
Wireshark
John the Ripper
Frequently Asked Questions
Browse through the FAQs given below to find answers to the commonly raised questions related to the VAPT services
Network VAPT is carried out in accordance with the guidelines of NIST SP800-115, PTES, CIS Benchmarks.
Besides periodic VAPT, it is also advisable to perform device-level security analysis along with configuration audit as per OEM’s recommended security policies and procedures.
It is highly recommended to carry out VAPT once every 6 months to identify any potential network intrusions and gaps.









