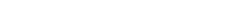Cyber Security
- Home
- Cyber Security
// Cyber Security, Functional, Usability & Performance
Secure Your IT Infrastructure With Us
Most Cyber security tools today focus on visibility and blocking at the point of entry in order to protect systems. However, the proliferation of threats far outpaces these network defence tactics, and the subsequent gap can never fully be closed. No new technology will adequately address this security dynamic. Instead, a new criterion is required: a defence model that detects, mitigates and remediates pre, during, and post an attack.
For Over 6+ Years.
For Millions of Users
Codeekte provides complete suite of manual and automated security testing services.
Security methods must focus on both detection and the ability to mitigate the impact after an attacker gets in. We look at your security model holistically and gain visibility and control not just at the endpoints but across the extended network and the entire attack continuum before an attack happens, during the time it’s in progress, and after it has damaged systems or stolen information.
A website is a handbook for your online audience to know about your business and services, and a good design is like a cherry on the cake.
LEARN MOREWebsite Development

CODE EKTE is one of the most experienced and well-established mobile application development companies that has been offering life changing digital experiences since 2017.
LEARN MOREMobile Application

Digital Marketing Services, we are here to help you to grow your business revenue. We have unique marketing solutions for your unique business.
LEARN MOREDigital Marketing

Comprehensive Cyber Security Suite
Our team can assist you in transforming your business through latest tech capabilities to stay ahead of the curve. provides a complete suite of leading-edge cyber security products.
- VAPT Security Services
- APPLICATION SECURITY TESTING
- NETWORK SECURITY TESTING
- CLOUD SECURITY TESTING
- SECURE CODE REVIEW
- IOT DEVICES SECURITY TESTING
Secure Your IT Infrastructure With Us
Active Clients
projects done
team advisors
Glorious Years
Business Industries
What We Serve

APPLICATION SECURITY TESTING
Web and Mobile Applications are the primary entry point for attackers. These apps are often left vulnerable due to factors like enormous pressure on Development teams to meet deadlines, vulnerable third-party APIs.

NETWORK SECURITY TESTING
Network management of any organisation is one of the easiest target for attacks. Wireless Networks are highly vulnerable to attacks like MiTM, DoS and De-Authentication attacks. Network is also vulnerable to DoS Attacks etc.

CLOUD SECURITY TESTING
Securing cloud infrastructure is important aspect of digital mobility. Most cloud migration services focus of speed rather than security. Multiple data breaches have taken place due to misconfigured cloud services.
IOT DEVICES SECURITY TESTING
IOT devices are connected to technology and therefore can be easily manipulated. Hackers can hack these devices and can disrupt the functionality of these devices. These attacks can either lead to a device being non-functional or it can be misused by the attacker.

SECURE CODE REVIEW
A secure code review is the process of identifying and patching coding errors in the development phase before they turn into a high-level security risk. The review helps in identifying hidden vulnerabilities, design flaws, detect insecure coding practices.

VAPT Security Services
Security Audits are necessary and mandatory for continuous evaluation of the security safeguards for any organization. Vulnerability Assessment is a process of discovering flaws that affect an information system. It is an in-depth evaluation of security weaknesses in the organization.

Gaming-media & Enterteinment

Information Social Networking

Game Industry

Retail & E-commerce

Government Industry

Business & Finance

Banking / Finance Industry