Application Security Testing?
- Home
- Application Security Testing?
What is Application Security Testing?
The purpose of this assessment was to evaluate the cyber security of your Web Application using simulated attacks to identify and exploit vulnerabilities in your Web Application. Malicious attacks are simulated using a variety of manual techniques supported by automated tools. Our penetration testing methodology goes beyond the detection process of simple scanning software to identify and prioritize the most vulnerable areas of your Web Application and recommend actionable solutions.
Talk To A Security Expert
We Will Help You To Choose The Best Plan!
CODE EKTE’S verbose technique for web application entrance testing overlay the classes of weaknesses in the Open Web Application Security Project (OWASP) Top 10 2017, including however not restricted to: Injection, Broken Authentication, Sensitive Data Exposure, XXE, Broken Access Control, Security Misconfigurations, XSS, Insecure Deserialization, utilizing parts with Known Vulnerabilities, thus more. Every single web application entrance test is directed reliably utilizing internationally acknowledged and industry standard systems. To guarantee a sound and extensive application entrance test, CODEEKTE use industry standard systems as an establishment for completing infiltration tests.
Industry’s Best Security Standards
Our team of experts uses practices that involve the industry’s best security standards including:
OWASP Secure Coding Guidelines
- Input Validation
- Session Management
- Cryptographic Practices
- Communication Security
- Database Security
- Memory Management
- Authentication and Password Management
- Output Encoding
- Access Control
- Error Handling and Logging
- System Configuration
- File Management
- General Coding Practices

SANS25 Secure Coding Guidelines
- Out-of-bounds Read, Integer Overflow or Wraparound
- Improper Restriction of Operations within the Bounds of a Memory Buffer
- Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')
- Exposure of Sensitive Information to an Unauthorized Actor
- Use After Free, Improper Authentication
- Cross-Site Request Forgery (CSRF), Missing Authorization
- Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection')
- Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal')
High Level Test Cases
Test Cases for Black-Box Assessment:
- Information Gathering
- Data Validation Testing
- Configuration and Deploy Management Testing
- Cryptography
Test Cases for Grey-Box Assessment:
- Identity Management Testing
- Authorization Testing
- Input Validation Testing
- Authentication Testing
- Session Management Testing
- Business Logic Testing
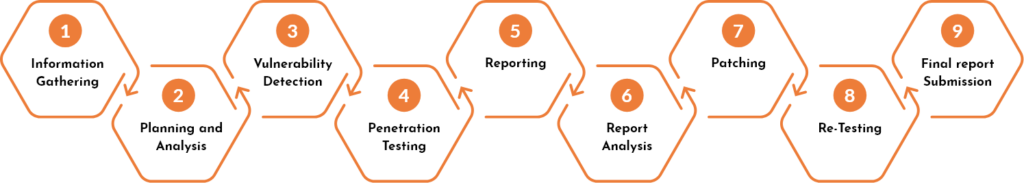
Security Testing Methodology

01
RECONNAISSANCE
The primary stage in a web application infiltration test is centered around gathering however much data as could reasonably be expected with regards to an objective application. Surveillance, otherwise known as Information Gathering, is one of the most basic strides of an application pen test. This is done using public devices (web indexes), scanners, sending straightforward HTTP demands, or exceptionally created demands. Therefore, it is feasible to compel the application to spill data, e.g., unveiling blunder messages or uncovering the renditions and innovations utilized.
Model testing include: Conduct Search Engine Discovery and Reconnaissance for Information Leakage, Search Engine Recon, App Enumeration and App Fingerprinting, Identify application section point
02
CONFIGURATION MANAGEMENT
Understanding the conveyed design of the server/foundation facilitating the web application is close to as basic as the application security testing itself. All things considered, an application chain is just pretty much as solid as its most vulnerable connection. Application stages are wide and shifted, however some key stage setup blunders can think twice about application similarly an unstable application can think twice about waiter (unreliable HTTP techniques, old/reinforcement documents).
Model testing incorporates: TLS Security, App stage setup, File Extension Handling and Cross Site Tracing, Test HTTP severe vehicle security, Test HTTP techniques, Test File consent

03
AUTHENTICATION TESTING
Authentication is the process of attempting to verify the digital identity of the sender of a communication. The most common example of such a process is the log on process. Testing the authentication schema means understanding how the authentication process works and using that information to circumvent the authentication mechanism.
Example testing includes: Weak lockout mechanism, Bypassing authentication schema, Browser cache weakness, Weaker authentication in alternative channel.
04
SESSION MANAGEMENT
Session Management is defined as the set of all controls governing the stateful interaction between a user and the web application he/she is interacting with. In general, this covers anything from how user authentication is carried out, to what happens when they log out.
Example testing includes: Session Fixation, Cross Site Request Forgery, Cookie Management and Session Timeout, Testing for logout functionality.


05
AUTHORIZATION TESTING
Approval Testing includes seeing how the approval cycle functions and utilizing that data to evade the approval system. Approval is a cycle that comes later an effective validation, so the pen analyzer will confirm this point later he/she holds substantial certifications, related with a distinct arrangement of jobs and honors. Subsequently, it ought to be checked assuming it is feasible to sidestep the approval mapping, track down a way crossing weakness or track down ways of heightening the honors
Model testing incorporates: Directory Traversal, Privilege Escalation and Bypassing Authorization Controls, Insecure direct item reference.
06
DATA INPUT VALIDATION
The most common web application security weakness is the failure to properly validate input coming from the client or from the environment before using it. This weakness leads to almost all of the major vulnerabilities in web applications, such as cross site scripting, SQL injection, interpreter injection, locale/Unicode attacks, file system attacks, and buffer overflows. Example testing include: Cross Site Scripting, SQL Injection, OS Commanding and Server- Side Injection, code injection, Local file inclusion and Remote fie inclusion, Buffer overflow

07
TESTING FOR ERROR HANDLING
Regularly, during an infiltration test on web applications, we face numerous mistake codes created from applications or web servers. It’s feasible to make these mistakes be shown by utilizing a specific solicitation, either uniquely created with instruments or made physically. These codes are exceptionally helpful to infiltration analyzers during their exercises, since they uncover a great deal of data about information bases, bugs, and other innovative parts straightforwardly connected with web applications.
Model testing include: Analysis for Error codes, Analysis for Stack Traces.
08
TESTING FOR BUSINESS LOGIC
There are many examples that can be made, but the one constant lesson is “think outside of conventional wisdom”. This type of vulnerability cannot be detected by a vulnerability scanner and relies upon the skills and creativity of the penetration tester. In addition, this type of vulnerability is usually one of the hardest to detect, and usually application specific but, at the same time, usually one of the most detrimental to the application, if exploited.
Example testing include: Integrity checks, Process timing, Upload of unexpected filetype, Ability to forge request.

09
CLIENT-SIDE TESTING
Customer Side testing is worried about the execution of code on the customer, normally locally inside an internet browser or program module. The execution of code on the customer side is particular from executing on the server and returning the ensuing substance.
Model testing include: JavaScript execution, Client-side URL redirection, Cross beginning asset sharing and Manipulation.
10
DENIAL-OF-SERVICE (OPTIONAL)
A disavowal of administration (DoS) assault is an endeavor to make an asset inaccessible to its genuine clients. Customarily, refusal of administration (DoS) assaults have been network based: a vindictive client floods an objective machine with sufficient traffic to make it unequipped for overhauling its planned clients. There are, notwithstanding, sorts of weaknesses at the application level that can permit a pernicious client to make specific usefulness inaccessible. These issues are brought about by bugs in the application and regularly are set off by vindictive or sudden client input. This period of testing will zero in on application layer assaults against accessibility that can be sent off by only one vindictive client on a solitary machine. Not all customers have a craving for DoS testing, in this manner it may not forever be a part of every single entrance test.


11
REPORTING
The detailing step is expected to convey, rank and focus on discoveries and produce an unmistakable and noteworthy report, complete with proof, to the task partners. The introduction of discoveries can happen face to face design is generally helpful for imparting results. At Codeekte, we believe this stage to be the most significant and we take extraordinary consideration to guarantee we’ve imparted the worth of our administration and discoveries completely
Tools Used
We use industry benchmark security testing tools across each of the IT infrastructure as per the business and technical requirements.
Below are few from many of the tools we use:
Burpsuite
Nessus
Nmap
Acunetix
Net Sparker
DIRB
Frequently Asked Questions
Browse through the FAQs given below to find answers to the commonly raised questions related to the VAPT services
Vulnerability Assessment and Penetration Testing (VAPT) is a security testing methodology that is composed of two, more specific methods within the same area of focus. The test is undertaken to perform security vulnerability assessment and identify the exploitable security vulnerabilities in your organization’s IT infrastructure.
Network VAPT is carried out in accordance with the guidelines of NIST SP800-115, PTES, CIS Benchmarks.
Besides periodic VAPT, it is also advisable to perform device-level security analysis along with configuration audit as per OEM’s recommended security policies and procedures.
It is highly recommended to carry out VAPT once every 6 months to identify any potential network intrusions and gaps.
It is highly recommended to carry out VAPT once every 6 months to identify any potential network intrusions and gaps.









