Medical Device Security Testing
Medical Device Security testing: Cyber Security Assessment & Pretesting
Medical Device Security testing The healthcare industry is growing rapidly and has enormous IT infrastructure and loads of medical devices. Since these devices rely heavily on modern technology, they need to be secured against cyber threats and risks.
Vulnerabilities in medical devices are increasingly posing risks to the patients and those in need of healthcare. The aim of our assessment is to identify the exploitable vulnerabilities in these devices to secure them against attacks, eventually saving people’s lives.

Request a Sample VAPT Report

Request a Sample Certificate
Talk To A Security Expert
We Will Help You To Choose The Best Plan!
Objective of Medical Devices VAPT Assessment
Throughout our assessment, we meet all the protocols, cyber security compliance requirements, and industrial standards enforced by the regulatory authorities. In our cyber security analysis of medical devices, we assess the following –
- Existing Controls
- Data Flows and Use Cases
- Risks Related to Integrity and Confidentiality
- Review Product and Their Security Policy
- Technology Used in Products
- Architecture of Software from a Cyber Security Perspective
- Access to Devices and Systems
- Revision on Security Controls
- Medical Standards and Security Rule
Industry’s Best Security Standards
Our team of experts uses practices that involve the industry’s best security standards including:
Benefits of Medical Device Security Assessment & Penetration Testing
- We identify vulnerabilities and provide a complete threat assessment.
- We improve security controls and enhance the security features in the devices and systems.
- We prevent and repel cryptographic attacks or unauthorized access.
- We conduct packet analysis and implement the most suitable protocols in the communications.
- We improve the security and auditing reports of the medical organization.


Based on the Analysis, We May Recommend the Following Changes
- Change in design to reduce risks
- Modifications in controls
- Architecture, PKI, Hardening, Encryption, Blockchain, and several other technologies in products
- Modifications in architecture to enhance security
- Redefining accessibility for devices and systems
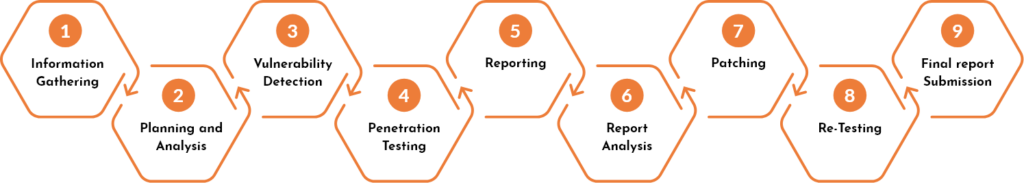
Medical Devices VAPT Methodology
There is a meticulously designed process involved in our medical device security assessment and penetration testing. Here are the steps we follow to assess the security of these devices.

01
INFORMATION GATHERING
Initially, we prepare feasibility analysis during onsite assessment. We collect basic information about your medical facility after discussing it with your team. We review your policies and documentation associated with medical practices and devices. The aim is to comprehend the customized understanding of your medical institution and formulate a course of action with a set strategy. This will allow us to utilize time and conduct onsite assessments.
02
PLANNING
The collected information provides a comprehensive idea of the situation and requirements. Then, we conduct a detailed analysis of the gathered information through research. It will help us segregate the collected information in fragments to set objectives for further steps and final outcome. These objectives are then presented to clients to align the goals and proceed to the next step.


03
VULNERABILITY DETECTION
This stage involves testing and evaluating your medical institution in-person. We will travel to your facility and perform a complete cyber security assessment. It will include security evaluation, exploitation, and penetration testing. We can also conduct testing at Kratikal’s workplace if you send your devices and system to us. We will conduct penetration testing and explore vulnerabilities to get access into the system through USB, LAN, Ports, Ethernet, HDMI, etc.
04
PENETRATION TESTING
We explore different vulnerabilities in the devices and systems. Then, we list out most critical vulnerabilities and conduct penetration testing. The major portion (about 80%) of VAPT is carried out in this stage. We develop customized scripts based on the target device and exploit each vulnerability manually.


05
REPORTING
The reporting is crucial for maintaining records and presenting our assessment in a proper manner. The purpose of reporting is to take prioritized approach for solution with complete evidence provided to the clients and stakeholders. At CodeEkte, we allocate services to implement the strategies that we devise to eliminate all the vulnerabilities detected during the assessment. After reporting is done, we send and review it on a web-call.
06
RE-TESTING
In this step, we evaluate all the findings of the previous five steps and categorize them based on different parameters. We create a list of the vulnerabilities and mark whether they are fixed or not. The main objective of re-testing is to ensure that no vulnerabilities are left after the completion of security patches and updates. The results become a benchmark that will eventually enhance the security of medical systems and devices. The findings of this step is communicated to clients based on the level of risk.

Why Choose Us for Medical Device VAPT?

- Information Integrity
With our assessment, we provide trustworthiness and dependability of information with consistency, accuracy, and reliability.
- Mult-dimensional Approach
We conduct multi-layered assessments to exploit vulnerabilities and at the same develop security measures that need to be implemented.
- Trust and Ethics
We value ethics over anything else and our procedure is purely intended to strengthen cyber security in your medical institution by developing and incorporating trust with our clients.
- Proactive Procedure
Our main motive is to secure medical devices, so that they cannot be exploited by attackers by taking a proactive approach to detect the vulnerabilities and resolve them before they’re exploited.
- Effective Results
We are dedicated to sustaining a level of expertise in order to provide effective results just as we have done many times for our clients in the past.
Tools Used
We use security testing tools that meet the industry benchmarks across every domain of IT infrastructure. These tools are applied based on business and technical requirements. We use numerous tools and some of them are listed below:
Burpsuite
Nessus
Nmap
Wireshark
Metasploit
Frequently Asked Questions
Browse through the FAQs given below to find answers to the commonly raised questions related to the VAPT services
What is Healthcare Cyber Security?
Cyber security in the healthcare domain refers to protecting and securing the medical devices and systems containing digital data or information. The assurance of security in health care refers to the protection of data and medical records of the hospital or any medical facility.
What are the cyber security certifications in Medical Security?
The most prominent certification in medical cyber security is HCISPP (HealthCare Information Security and Privacy Practitioner) which is provided by (ISC)^2 which stands for International Information System Security Certification Consortium. Other certifications are
- CPHIMS (Certified Professional in Healthcare Information & Management Systems)
- CHDA (Certified Health Data Analyst
- CAHIMS (Certified Associate in Healthcare Information and Management Systems)
What are medical device cyber security standards?
US FDA (United States Food and Drugs Administration) is the internationally recognized standard that provides guidelines associated with medical technology and software applications. EU R (European Union Regulation) is also a standard that lags behind US FDA. They provide regulations harmonizing ISO regulations and security provisions.
What are the cyber risks in healthcare?
Major cyber risks and threats in the healthcare and medical sector are –
- Data breaches
- Malware and Ransomware
- DDoS (Distributed Denial of Service) attacks
- Insider Threats
- Phishing Attacks
- Cloud Threats
What is meant by ‘HIPAA Compliance Requirements’?
HIPAA stands for Health Insurance Portability and Accountability Act of 1996. This act governs 6 requirements that are essential for an organization to get HIPAA Compliance. These requirements are –
- Remediation Plans
- Self – Audits
- Documentation
- Policies, Procedures, and Employee Training
- Incident Management
- Business Associate Management
What is the HIPAA Penetration Test?
HIPAA Penetration Testing is conducted under HIPAA Security Rule which is carried out by a data security analyst. The objective of this test is to identify vulnerabilities and weaknesses in data security. This type of testing is known as ethical hacking.
A Vulnerability Scan is a process of proactive identification of vulnerabilities in the application, network, and security. The process of scanning is done by a third-party service provider which examines the access to devices and networks.